Event: Stopping an OT attack - hands on demo
Learn how to detect and block a typical OT attack with a team of experts that use the latest technology of visibility and security
Thursday 25 May
10h00 - 12h00
Overview
One strong trend within the change of the cybersecurity threat landscape is that adversaries seek to compromise industrial networks. However most CISOs agree with the importance of protecting ICS segments of the network, this approach on hand seems to require tremendous effort and in many cases lacks a clear, holistic defense strategy. In many organizations, there are different maintenance and operations teams for the office IT and the industrial IT – referred to as OT. Deriving from this status quo sometimes the OT management independently decides about the cybersecurity or the IT departments follow an air-gap or segmentation strategy.
In this demonstration you will see (and touch) the components of a typical industrial network (PLC, HMI, OPC server, analogue devices, network switches) and the physical and software tools from Keysight which make visible the network traffic and the potential malicious behavior.
SOCWISE have built up and operates a fusion SOC, which means that both IT and OT security is covered by a respective strategy, containing slightly or dominantly different elements on all people, process, and technology layers. On the people layer, there are mostly similarities, meaning threat awareness and individualized competence development for each specific role is the way to follow. On the process level, the difference is more significant due to the different priorities - having safety first, which is closely followed by continuity in production. There is just limited flexibility within OT processes, but on the other way, the complexity of them might be lower – especially using the tools we present. Through the technology layer, there are both similarities and differences. The similarity is brought by the leading trend of production digitalization, which results in similar technologies to grow (server-client infrastructures, cloud, IoT, machine learning, digital twin, etc.), but still, the non-intrusive nature of security tools is a must and due to the utilization of industrial network communication protocols another portfolio of sensors and perimeter security instruments are necessary.
What is a Fusion SOC?
Fusion SOC is the security operations capability or organization that is responsible for the detection and response of both IT and OT networks.
Learn how an attack happens in an ICS network and how an expert team handles it!
The following technologies are leveraged for the demo:
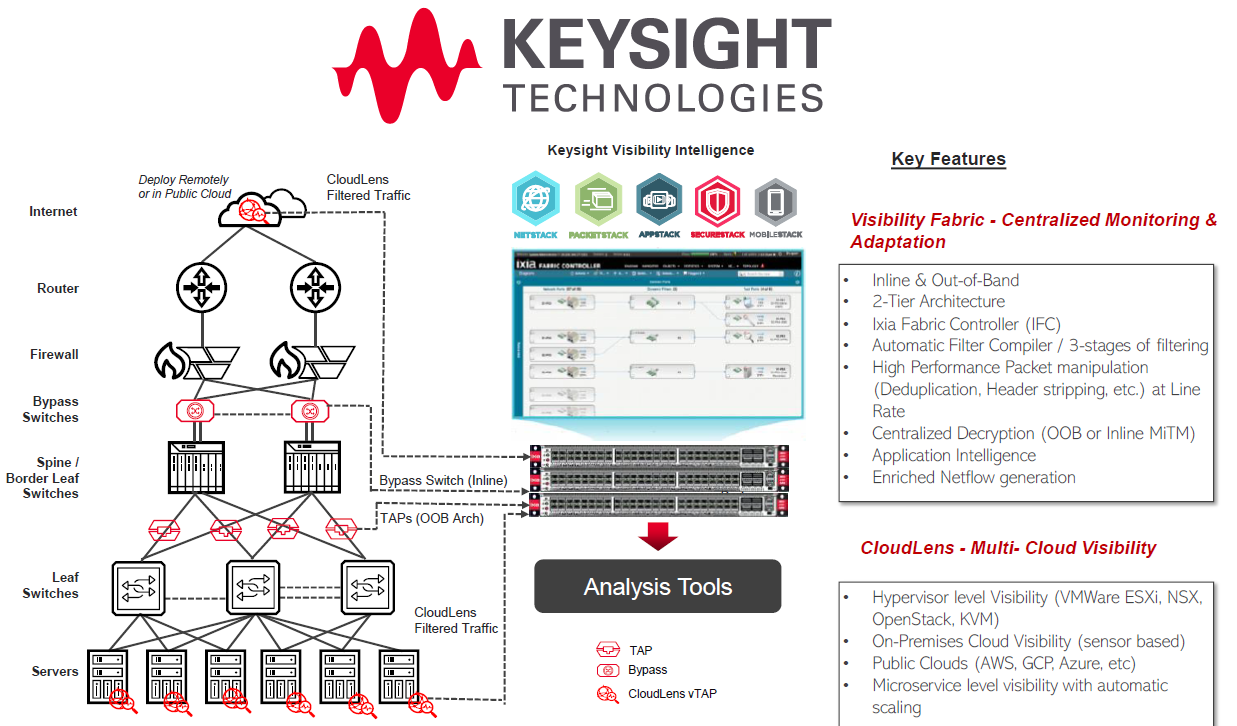
- Keysight IXIA Industrial visibility tools (TAP, packet broker)
- TxOne’s Edge IPS for network security and Stellar OT endpoint security
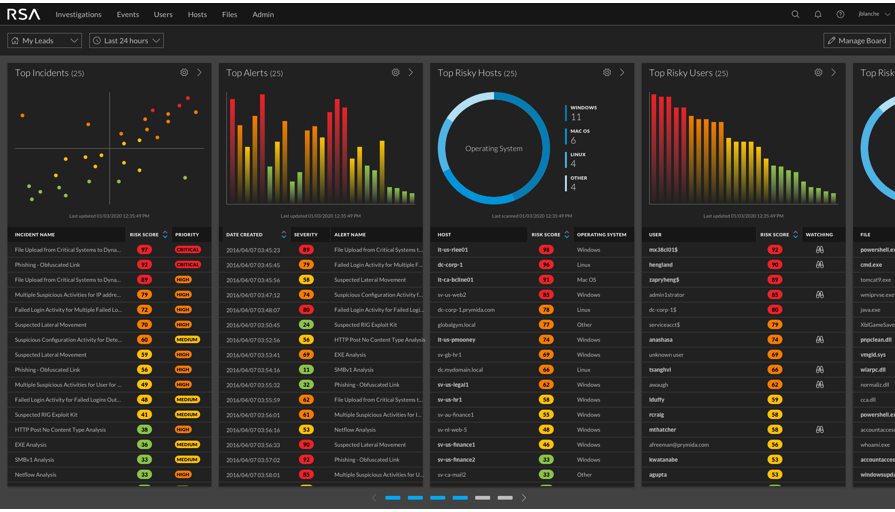
- NetWitness SIEM-SOAR SOC platform
- Siemens PLC, HMI
Speakers
About this session
For Who?: IT and OT Professionals having industrial communication anywhere within company
Date: Thursday 25th of May, 2023
Time: 10h00 - 12h00 (Livestream)
Agenda
10:00 - Start Webinar, introduction
10:30 - OT attack and response live demo
11:10 - Presenting the products leveraged
11:40 - Open discussion, touch and feel
12:00 - End of the webinar
REGISTER HERE
Please complete your details to register:
By completing this form, you agree to the use of your personal information in accordance with the Arrow Electronics & SOCWISE Privacy Policy and Terms of Use.